See Wiz In Action
The #1 Cloud-Native Security Platform
See how Wiz can detect and prioritize critical risks in your containerized environments.
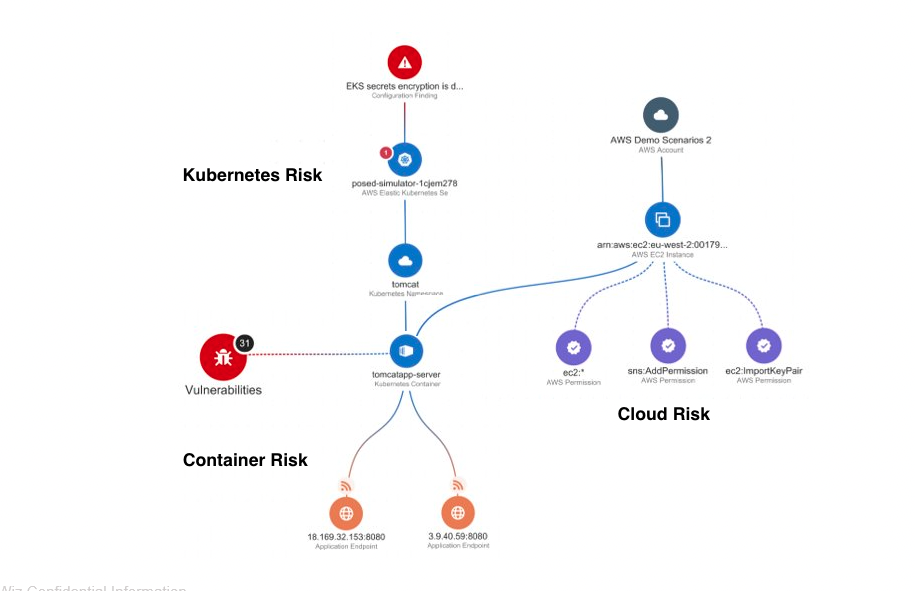
Container Security
Secure Everything From Containers To Cloud
Get complete visibility and prioritize critical risks across containers, Kubernetes, and cloud environments.
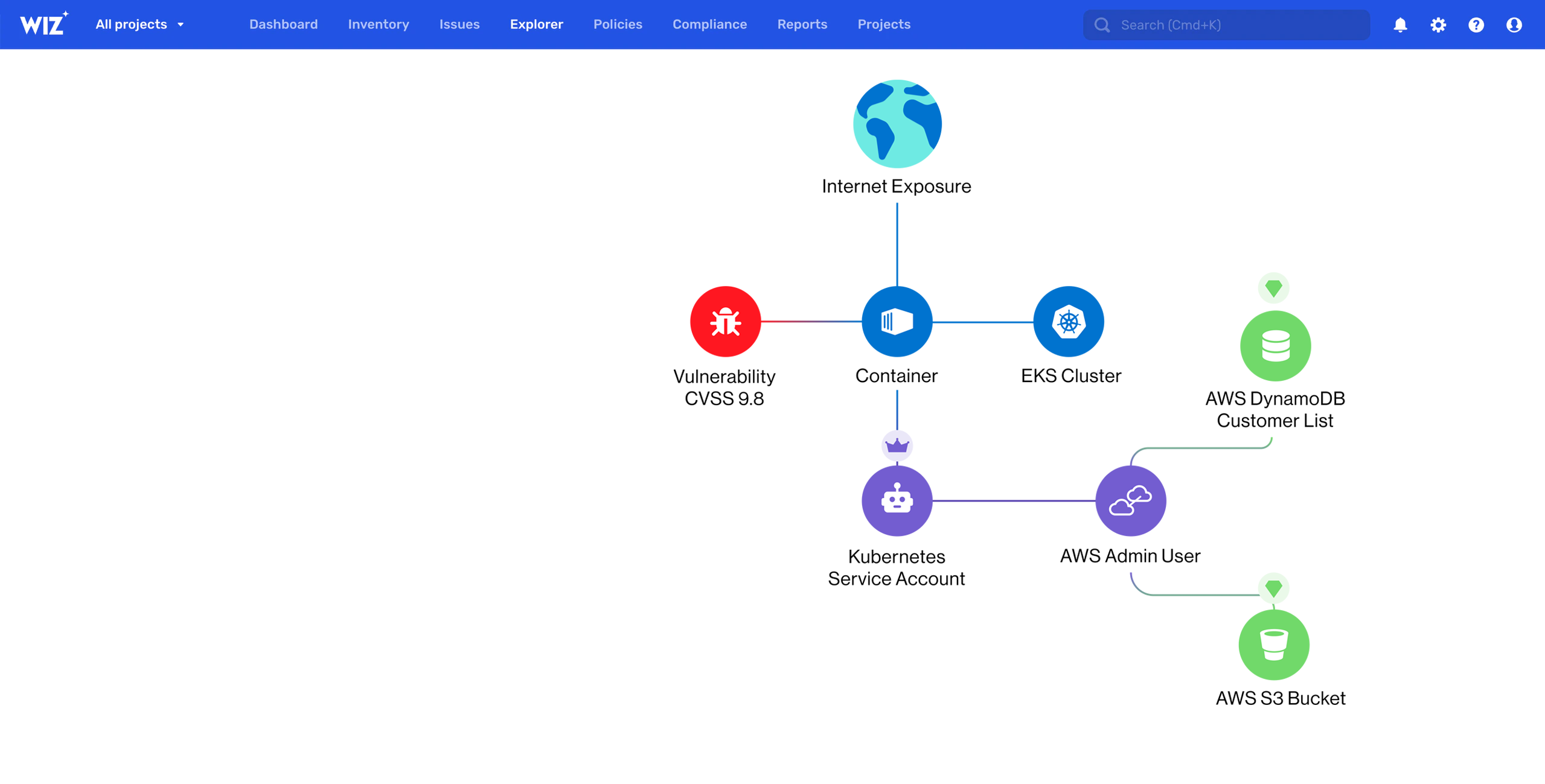
Secure All Your Cloud-Native Applications
Prevent Attack Paths At Every Step
Rapidly build containerized applications without risks. Holistically secure containers, Kubernetes, and cloud environments.
Complete Visibility
Discover and scan all your containers, hosts, clusters, and cloud to build a complete view of your containerized environments.
In-Depth Risk Assessment
Correlate and prioritize container risks with Wiz's Security Graph to detect vulnerabilities and harden your clusters.
Shift Left
Secure container images from the developer's sandbox into run-time and ensure security compliance while deploying.

CISO | FOX


Development Manager



The Companies You Trust Trust Wiz






Meet the speakers

Nir Ohfeld is a security researcher at Wiz Research. Nir currently does cloud-related security research at Wiz. Nir specializes in the exploitation of web applications, application security and in finding vulnerabilities in complex high-level systems. Nir was also featured 3rd on the MSRC Top Security Researcher Leaderboard.

Rotem Lipowitch is a threat researcher at the Wiz Research team with broad experience in the cyber security world. She specializes in emerging cyber security threats, vulnerability analysis, researching and developing new ways to detect cyber security threats.

Avigayil was a product manager at Intezer, leading Intezer Analyze product lifecycle. Prior to this role, she was part of Intezer's research team where she focused on malware analysis and threat hunting. During her time at Intezer, she has uncovered and documented different malware targeting both Linux and Windows platforms.

Scott is a threat researcher and cloud security historian. He previously secured the AWS environments of large companies, and consulted on AWS security to companies of all sizes and industries around the world.

Rotem Lipowitch is a threat researcher at the Wiz Research team with broad experience in the cyber security world. She specializes in emerging cyber security threats, vulnerability analysis, researching and developing new ways to detect cyber security threats.

Nir Ohfeld is a security researcher at Wiz Research. Nir currently does cloud-related security research at Wiz. Nir specializes in the exploitation of web applications, application security and in finding vulnerabilities in complex high-level systems. Nir was also featured 3rd on the MSRC Top Security Researcher Leaderboard.

Lorem ipsum dolor sit amet
Lorem ipsum dolor sit, amet consectetur adipisicing elit. Deserunt, dolores exercitationem tempore, assumenda unde vero quaerat, illum cupiditate quae, necessitatibus sed commodi quis nisi quos. Vitae, tempore? Molestiae, eligendi adipisci provident consequatur inventore. Reprehenderit sequi possimus maiores voluptates aliquam veritatis?
Lorem ipsum dolor sit amet
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Additional Resources

Cloud Security Posture Management (CSPM) Buyer’s Guide

Wiz for CSPM technical whitepaper



